Before we get started, there are a few “Quid Pro Quos”
- I did not promise this would be easy (though once you understand it, it is pretty simple).
- Always follow your security guidelines and practices. This reveal does require the use of a 3rd party software. Use at your own risk and only in a sandboxed or segregated system.
- Be sure to read the terms and conditions set forth before moving on.
- “I can’t make anybody fall in love.” – Genie
The Message:
On October 24th we sent out a message titled: “Ok GOVITnites, Session Spotlight & GOVIT Easter Egg Challenge – Are You In?” If you didn’t receive this then you were late in registering and you’ll just have to follow along.
The Clue:
Because it was October and Cybersecurity Awareness Month, we thought it was appropriate to do some real-world show and tell, ethical style hacking (within our own messaging). Hiding an easter egg behind our veil of bits and bytes. Or “masking” our file – all appropriate for Halloween and Cybersecurity Awareness Month. Yes, it can also be a tad bit scary!
Radio Edit:
We used a form of writing dating back to medieval literature called Acrostic to give you the first clue in this easter egg challenge. In this first clue you had to have a keen eye. In subsequent emails we hinted at “taking a shot” to find the egg – referring to the bulleted items (clever, I know). (If anyone knows who writes the Winter Carnival medallion hunt clues – hook me up).
Okay, Charles, what does “Find OpenStego” mean? Well, just that, go out and find OpenStego.
OpenStego is a steganography application that provides two functionalities: Data Hiding: It can hide any data within an image file.
Ding! Ding! Ding!
Yes! Our easter egg is hidden inside an image file! You can do that?! Mind blown!
Refraining from sharing this with your teenagers is completely acceptable.
Pretty cool huh?
This is no ordinary logo! It once changed the course of an attendees life.
An attendee who, like this logo, was more than what they seemed – a diamond in the rough.

So, how do we get to crack this egg? As in our quid pro quos, please take the next step with caution and always use a sandboxed or segregated system when working with unfamiliar 3rd party applications.
Cracking the Egg:
Step 1: Right click on the logo and save to an accessible directory.
Step 2: Install/Open the OpenStego Application
As you can see, we’ve deployed OpenStego in our Windows Sandbox.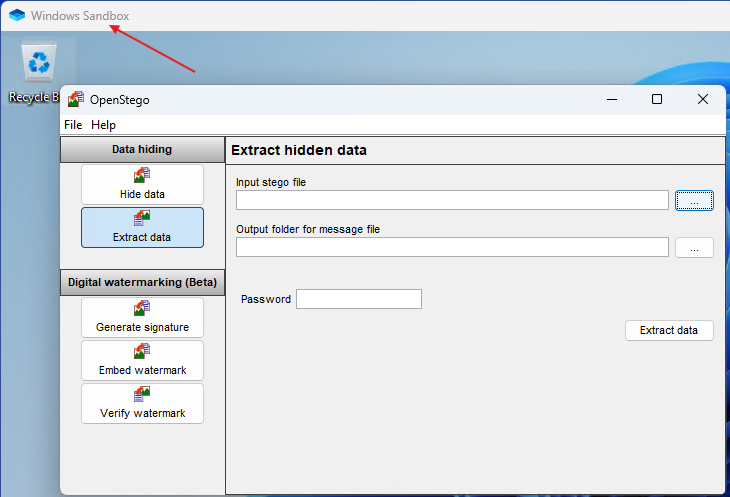
Step 4: Click on the Extract Data button and enter in the “Input stego file” (where your image was saved) and the Output folder for the message file.
Step 5: Click on Extract Data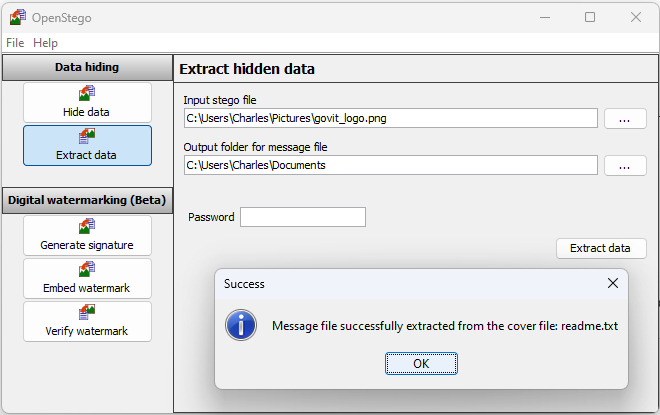
Holy Cow! Batman! There is a file embedded in the png file!
Step 6: Let’s go see what is in the readme.txt file.
“Congratulations! Send the following quote for eternal glory!
“Technology is a useful servant but a dangerous master”
– Christian Lous Lange”
Something to ponder as you look to attend the 2024 GOVIT Leadership Summit and Symposium.
This quote highlights the dual nature of technology: it’s immensely beneficial when we control and direct its use, but potentially harmful when it gains dominance over us. When technology is our “servant,” it simplifies tasks, amplifies our abilities, and can make life richer. But as a “dangerous master,” technology can erode personal privacy, increase our dependency, or even displace our humanity, like when we feel more controlled by our devices or overwhelmed by an endless stream of information. In essence, it’s a reminder to approach technology with mindfulness and intentionality. We should harness its power to enhance human welfare and avoid becoming overly reliant or entrapped by it.